
Photocredit: Stephen Coles; https://www.flickr.com/photos/stewf/
Is Email Phishing Unstoppable?
Just don’t rely too much on your office antivirus software.
Your antivirus software ~might~ be good at stopping viruses, but they’re becoming more irrelevant every day at protecting your data and devices.
Some experts are pointing to a recent warning by the U.S. Department of Homeland Security’s Computer Emergency Readiness Team (CERT), where they issued a warning about global security product Symantec and Norton Security products containing dangerous vulnerabilities.
This doesn’t mean they’re completely useless and they don’t perform an important function. There’s a more important reason to not blindly trust your antivirus software to keep your data safe.
People tend to rely too much on them, giving them a false sense of security.
Evolving Threat Tactics
 Just a few short years ago, antivirus software protected against 80 to 90 percent of online threats. Today, it’s more like 10 to 20 percent because of constantly evolving threat tactics.
Just a few short years ago, antivirus software protected against 80 to 90 percent of online threats. Today, it’s more like 10 to 20 percent because of constantly evolving threat tactics.
While some company executives feel smugly confident about their level of antivirus security, cyber criminals are getting in through the company’s weakest links—the users.
An alarming trend is the aggressive growth of phishing techniques used by attackers in 2016.
Hackers are spending less effort on circumventing installed security software products like Symantec, and are doubling-down on phishing tactics that trick unwary users into letting them in.
Probably because it’s working.
Phishing surged 250 percent in the first three months of 2016
The Phishing Activity Trends Report Q1 2016 by APWG.org (Anti Phishing Working Group), says the surge in phishing attacks in Q1 this year has grown more than in any other three-month period since tracking began in 2004. The growth is staggering.
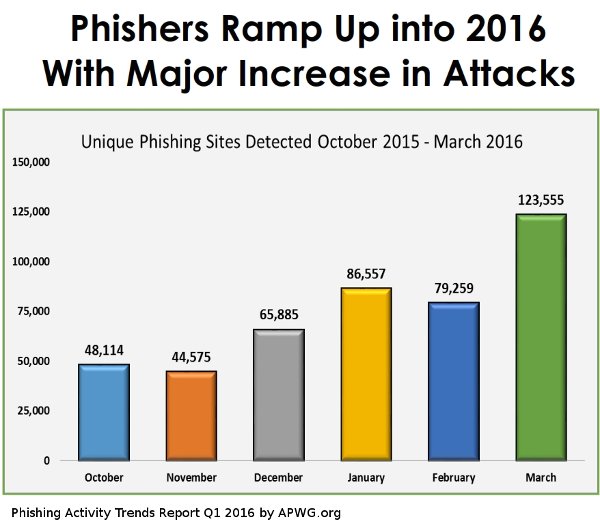
This year, there’s a corresponding jump in unique phishing sites as well. These attacks focus on sucking users in with so called social engineering or phishing to lure them into clicking onto compromised websites that will steal information or serve ransomware.
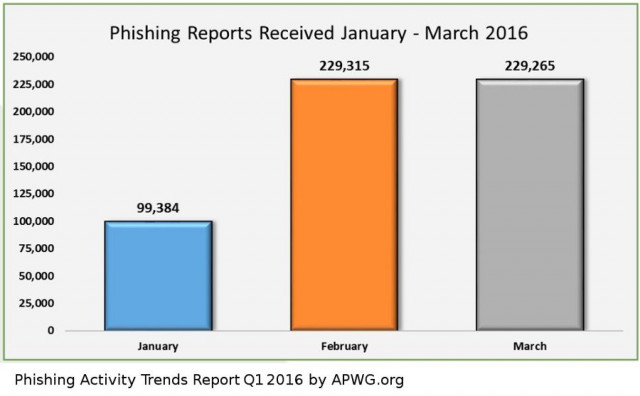
These phishing sites are usually short-lived, and are up just long enough to run their next campaign on a specific target. They move on to other targets long before antivirus services identify and blacklist.
While most phishing attacks start with the user triggering access for malicious code, what they really want is to drain your company bank accounts, computers to “bots” they control, to leverage access into corporate networks, and other future compromises.
You can find more detailed descriptions and motives for phishing in a post we published a couple of months ago titled “Phishing in the Office Pool”.
So just how effective is phishing?
Earlier this year, Verizon published the 2016 Verizon Data Breach Investigations Report. In it, they reported on that in 2015 there were 9,576 reported phishing incidents, 916 of them confirmed breach of data.
These are not small-time amateurs. 9 percent of last year’s phishing campaigns were conducted by organized crime syndicates, and about 9 percent by state-sponsored actors.
They report an astonishing 30 percent of phishing emails were opened by the target across all campaigns last year. It took a recipient an average of one minute 40 seconds to open the email and three minutes 45 seconds to click on the malicious attachment.
While phishing has been around for years, employees still struggle to identify a phony email.
What can you do?
Number One: Train Your Employees
Phishing awareness training is more important than ever now. It’s 2016, everyone should know how to spot a phishing attempt — both at work and at home.
For starters, Tripwire has a good “how to spot a phish” page at http://www.tripwire.com/state-of-security/featured/phishing-frenzy-the-good-the-bad-and-how-you-can-protect-yourself/ . It’s a couple of years old but still a good source to read.
Trainings services like PhishMe.com are leading the way with new training programs and services.
For your IT department, here are a few suggestions
- Use a good Email Spam Filter as your first line of defense, and set it high.
- Start talking about phishing. For example, supplement awareness training with emailed updates of recent attacks you’ve stopped. Forward recent data breach stories you receive as examples of careless behaviour and what can happen. Keep awareness of phishing current and fresh.
- Encourage employees to report any phishing emails they receive. Even better, create an easy way for them to report them – like an phishing alert email address, or a link on their dashboard.
- Enforce the use of Strong Passwords. We can’t say this enough (apparently).
- Protect the rest of your network from compromised desktops and laptops by segmenting the network and implementing strong authentication between the user networks and everything of importance.
- And for Pete’s sake, encourage users to come forward to admit they “may have made a mistake”. Phishing is getting sophisticated and it’s an easy mistake to make. The earlier it’s reported, the better chance you have of isolating and removing it before any damage is done.