
DDoS Attacks: What to Expect & How to Mitigate
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources.
We’re talking about DDoS attacks today because they are so common now that most organizations in North America have experienced some form of DDoS attack in the last 12 months.
In fact, one third of all downtime incidents are attributed to DDoS attacks, according to the worldwide Digital Attack Map (operated by Google Ideas and Arbor Networks).
The New Botnet Armies
Cyber attackers spend a lot of effort to build armies of botnets – networks of infected computers – by distributing malicious software via websites, social media, emails, attachments and other devious ploys (see Phishing in the Office Pool, some staggering facts on phishing, your employees and corporate risk). Once infected, these botnet computers can be controlled remotely without their owners’ knowledge, and used like an army to launch attacks against any targets. Some botnets are millions of computers strong.
Launching Attacks
Botnets generate massive floods of traffic to overwhelm a target. Some floods are more connection requests than the server can handle, while others send huge amounts of random data to tie up their target’s bandwidth.
The New Botnet Economy
Disturbingly, botnet networks are appearing for rent in new specialized marketplaces for anyone to buy time on. For as little as $150, anyone can hire a week-long DDoS attack directed at their own designated targets.
DDoS attacks are growing in number, size and sophistication.
Recent DDoS Statistics
149% The number of attack activity is growing dramatically: Akamai reported an 149% increase year last year.
50 Million There were an estimated 50 million attacks last year—that’s one or two attacks every second of every day.
125 Million MPPS The fastest flood attack of 2015 reached 125 million packets per second (MPPS), driving a DDoS attack of 65 Gbps)
180 Million MPPS by March 2016, many DDoS flood attacks were passing 180 MPPS at Cloudflare.
196 Gbps – The largest DDoS attack reported in mid 2015
400 Gbps – new record DDoS attack reported in Q4 2015
500 Gbps – record DDoS attack size in January 2016
602 Gbps – May 2016. This last weekend recorded a huge increase in attack severity at websites for BBS website and Donald Trump.
6.88 Gbps is the average DDoS attack size, with about 1/3 of all attacks passing 5 Gbps.
20 Minutes The Average DDoS attack length was 20 minutes in 2015.
97% Assaults against infrastructure, rather than applications now account for 97% of all DDoS activity.
75% of attacks are UDP floods.
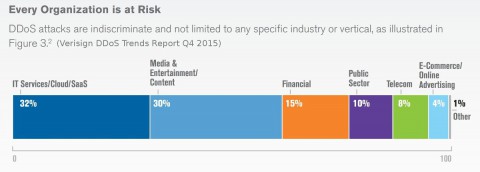
Financial Impact of a DDoS Attack
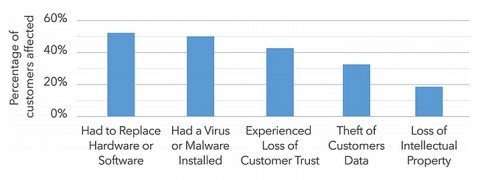
In late 2014, Incapsula surveyed 250 businesses with at least 250 employees. They found that almost 50 percent had been hit by a DDoS attack in the past. Of those, 91 percent had been in the previous 12 months, and 70 percent had two or more attacks. Most (86%) lasted less than a day, while 68 percent lasted less than 13 hours.
While short, the average estimated cost of these attacks were $40,000 U.S. per hour, for an average cost close to $500,000 per attack. The same Incapsula survey (below) found actual costs of attacks were broken down in by the following categories.
Common DDoS Attack Methods
You should also know that DDoS attacks are not limited to simple websites, like much of the news we read about. DDoS attacks are aimed to prevent your server or network resources from functioning, effectively blocking any access for employees or customers. Most DDoS attacks are usually one or more of three methods:
Network level attacks send massive amounts of “bots” traffic to overwhelm your connection capacity, blocking access to all connections to your network, website or online services. The worst of these attacks, like SYN floods and DNS amplification, will exceed 200 Gbps today. This is up from an average attack size of 10.1 Gbps in 2013.
Protocol attacks are designed to tie up server resources or intermediate communication equipment like firewalls and load balancers.
Application-level attacks attempt to overload resources on which an application is running. It crashes and your site goes down. They evade common security measures by mimicking legitimate user traffic.
Before choosing targets, an attacker will typically employ bots to probe a list of potential target sites for vulnerabilities they can exploit. When found, an appropriate attack methods are chosen and their game begins.
According to Imperva, over 80% of DDoS attacks see multiple methods used. Using smokescreen diversions, bypassing common protections and targeting multiple resources let them create the chaos they intend.
Attack mitigation and damage reduction. What can you do?
Realistically, most organizations will need some combination of on-premises attack mitigation capabilities and advanced external services. An honest assessment is always the first place to start. If you have good IT security staff in place, start with on-premises risk assessments first and evolve your strategy to include external services. If you don’t have IT staff or the required skill sets, start with a competent external service and look at adding managed CPE (customer premises equipment) mitigation capabilities in the future.
Here’s our list of Recommendations to Mitigate Future DDoS Attacks
There is no known way to stop or prevent a directed DDoS attack. Accept that it’s not always possible to defend against a large, organized DDoS attack without some impact to your network. In the event of an attack, the following recommends should help you to lessen that impact.
- Be proactive – assess your current system infrastructure and be prepared before your first (or next) attack.
- Identify any single points of failure in your network, like your DNS server or router and minimize any potential issues with them.
- Create a DDoS Response Plan. Define roles and responsibilities. Define consolidated reporting protocols. Determine what tools, resources and procedures you’ll use and become familiar with them.
- Learn how to identify signs of potential DDoS and other anomalous activity. Set up logging and alert reporting processes to assist with mitigation actions.
- Discuss with your ISP provider what they can do in case of a DDoS attack and consider options to implement.
- Invest in the right technology. Consider installing or upgrading load-balancers to balance traffic across multiple servers with the goal of creating additional network availability.
- Depending on your network infrastructure and data security needs, additional security appliances may be able to prevent assets from being compromised and provide additional protection from application layer attacks.
- Consider subscribing to a cloud-based anti-DDoS service to filter out malicious DDoS traffic or absorb with additional network capacity.
- Consider outsource contracting additional Managed Security Services from a competent IT Services firm (look here to see how Netcotech Network Solutions can help)
Since some DDoS attacks are engaged to disguise additional intrusion attempts, we also strongly recommend the following additional actions:
- I know this sounds basic, but be sure to secure ALL network resources in your infrastructure, not just those susceptible to DDoS attacks. Your goal is to prevent attackers from compromising servers, laptops, desktops and other resources that can be used to build botnets used for DDoS attacks from inside your network.
- Perform frequent scans on your web services network to patch or protect vulnerable web applications.
- Ensure all vendor patches for operating systems and network applications are always up to date.
Finally, we also recommend that you, or a network consultant you trust, literally walk through your network system and conduct the 6-Point Physical Network Checklist you will find in our blog post “Is Your Business Network A Hardened Vault Or A Cardboard Door?”