
Phishing in the Office Pool
Some staggering facts on phishing, your employees, and corporate risk
The term “PHISHING” covers a broad area. It’s arguably the most sinister form of cyber-attack, and it’s certainly the most common. And if you didn’t already know, it’s also considered as a major attack vector for entry into corporate and other network systems.
The United States Computer Emergency Readiness Team (US-CERT) defines phishing as a form of social engineering to solicit personal or corporate information by posing as a legitimate organization or known individual.
In other words, they’re looking for suckers to fall for some kind of scam.
While most phishing attempts target “people” in general, whether at work or at home, it’s their compromised passwords, computers and cell phones that become a risk to the organizations they work for, as well as others.

Phishing is deviously sneaky. The most common Phishing attempts are made through email, phone calls, texts, postal mail, social media, document attachments, websites and other means.
The bait is usually designed to trick people into responding to an action. The easiest to spot and avoid types promise us miraculous results, call out to us for hot times on lonely nights, appeal to our vanity, greed or desperation.
But increasingly, we’re seeing more sophisticated phishing attempts to spoof and mimic our friends, co-workers, favourite institutions and brands through trusted and “secure” channels like cell phones and social media accounts.
We are barraged with creative and sometimes realistic attempts to lure and encourage dupes to open documents, click on links, login (to fake online accounts), reply to sender, and reveal information or other seemingly benign actions.
How much has phishing grown? This chart shows the total number of unique phishing campaigns tracked by AntiPhishing.org
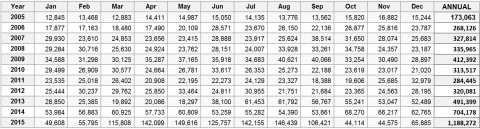
The number of unique phishing campaigns in 2014 grew 30% over 2013, and more than 41% last year over 2014. It’s growing because it’s profitable.
How does phishing pose a threat to organizations?
Usually, the goal of phishing is to reveal a password, install some malicious code, gain network or computer access, get past firewalls, disable antivirus software, to purchase non-existing miracle products, or some other equally undesirable action.
But the initial phishing attempt is usually just the first stage of a two- or three-stage play.
Their end-game is to use their new passwords, computer access or code installations for a variety of even more harmful activities–all aimed at draining your back accounts, adding computers to “bots” they control, to leverage access into corporate networks, and other future compromises.
These criminals know that the majority of people use a single, easily-remembered password for most, or all of their online accounts. If mistakenly given once, it might open all their bank accounts. That same password might also give them access to their work VPN, corporate network and secure databases too.
If phishers also manage to insert some code onto their device, they own it. They can access any personal details and other accounts information. They’ll probably use your private contact list and social media to spoof your friends, family and co-workers eventually.
How widespread is this, really?
At Microsoft, their Office 365 Exchange Online Protection system blocks 10 million spam messages every minute. Yep, that’s 10,000,000 per minute.
For another perspective, here’s a look at what just one antivirus provider –  Kaspersky Lab’s web antivirus – detected on their client sites during 2015…
Kaspersky Lab’s web antivirus – detected on their client sites during 2015…
(Kaspersky Lab ranks fourth in the global ranking of antivirus vendors)
1,966,324 – Malware infections that attempted to steal money via online access to bank accounts;
753,684 – Number of unique computers Ransomware programs were detected on;
121,262,075 – Unique malicious objects: scripts, exploits, executable files, etc;
798,113,087 – Attacks launched from online resources located all over the world;
34.2% – Percentage of user computers subjected to at least one web attack over the year;
6,563,145 – Number of unique hosts used by cyber criminals to launch their attacks.
Yet for all the money and effort we spend on detecting, neutralizing, protecting and stopping these attacks, we’re not exactly winning the war.
The next image shows the penetration of malware found on devices around the world last year.
In RED, the Top 20 countries with at least one malicious object was found on an average of 67.7% of computers, hard drives or removable media belonging to Kaspersky users.
That’s up from the 2014 figure of 58.7%
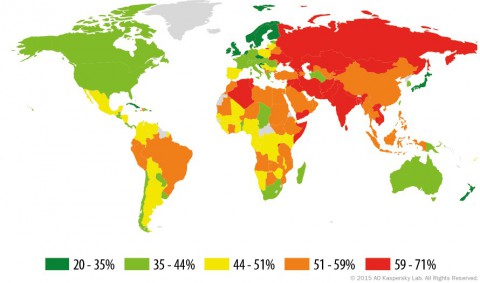
In light-green, Canada is considered to have a “moderate infection rate” of 39.2% of devices by Kaspersky Labs.
So it’s evident that people—our employees—are the best access into corporate networks for cyber criminals. If not by direct password or back-door entry, then eventually by DDoS, RansomWare or maybe another round of spear-phishing.
Last winter, Forbes reported on another company’s test of how phishing-savvy their employees are. 23 percent of workers fell for phishing mails, and 11 percent of the people that opened the mail also opened the fake malicious attachments.
If you think that’s bad…
Last year, JP Morgan was hacked in what was called the “largest theft of customer data from a US financial institution in history” when 76 million client records were stolen.
Just weeks later, a whopping 20% of JP Morgan’s staff fell for fake phishing emails sent to them as a test.
Even tech industry companies are not immune.
Just in March 2016, Pivotal employees received an email “from” their CEO Rob Mee, asking for payroll information. One admin employee, thinking the message was legitimate, sent the W-2 tax details for all 2,000+ U.S. Pivotal employees to an unknown party. Ouch.
Exactly the same thing also happened to Snapchat, Fast Company magazine, Seagate and RightSide in the same month.
These recent examples show how difficult a job IT and security professionals have in protecting your organization’s assets. It’s apparent that while a strong security system in place is important, employee education has to be part of the process.
All the hardware, software and backup systems we can spend our money on won’t help us if poorly trained people are still easily tricked into handing criminals the keys to the vault.
Follow this blog for more on this topic.
We’ll show you what your organization can do to better safeguard your assets, and your people.