
Cyber Attack Stats Reveal What Typical Target Companies Look Like
Surprise—it’s not the big companies we usually read about…
We’ve all seen the headlines about a national retailer or government organization getting hacked into, where either millions of client credit cards were stolen or huge databases of personal information were accessed and downloaded. These are the headline grabbers, and they happen almost weekly today.
Where it does happen, it often causes unimaginable grief, money and/or inconvenience for clients and customers; and panic, great expense and reputation loss for the target companies.

This week we show you some surprising facts uncovered by Ponemen Institute in a benchmark study sponsored by IBM.
What’s notable is that most hacking attacks are NOT on the high profile and billion-dollar companies. By far, the most common targets are small to medium size businesses where the average “take” is $15,000.
These are typically easier targets to crack and make up a hacker’s bread-and-butter revenue streams.
Hacking cost the global economy an estimated $445 billion dollars last year. That’s serious money at stake, and a serious incentive for criminal organizations to continue increasing their operations.

Time and Effort Facts about Targeted Attacks
70 HOURS OF ATTACK is how long it takes to break into a “typical”
IT infrastructure.
A “typical’ IT infrastructure is defined as:
- anti-virus in place
- vulnerabilities patching
- have some level of monitoring

147 HOURS OF ATTACK is how long it takes to breach an “excellent” IT infrastructure.
An “excellent’ IT infrastructure is defined as:
- anti-virus in place
- vulnerabilities patching
- have some level of monitoring
Plus
- consider every system end point (including laptops, smart phones, etc.)
- have an official IT Policy in place
- use administrative account control and password changes
- more robust, structured and regimented IT practices
206 HOURS OF ATTACK is the average amount of time when even the most persistent hackers will give up.
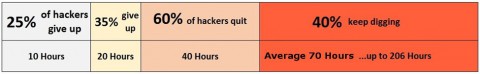
It’s safe to say that hackers are looking for easy targets–anything that takes less than 70 hours to breach is considered an easy target for an average payout amount of about $15,000.

Looking at the amount of time and effort a determined hacker is willing to invest, I would say that most companies are at moderate to severe risk of serious intrusion at some point in time.
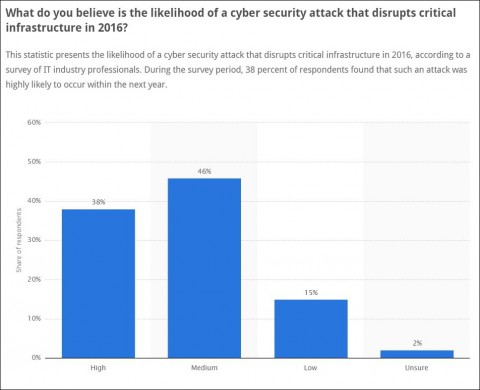
According to Statista.com, almost half of IT professionals surveyed in January 2016 believe their organization is at medium to high risk of a critical infrastructure disruption this year.
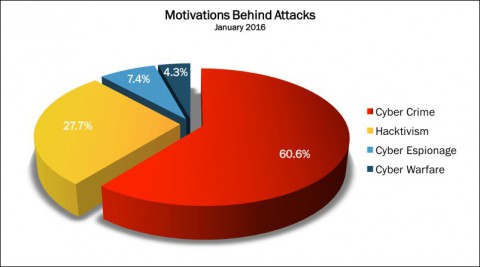
Profit is by far the leading motivation for hacking attempts, according to another recent survey from Hackmaggedon.com
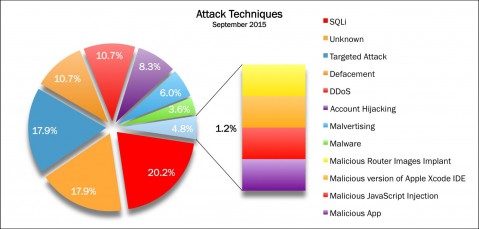
Risk Factors
How high the risk is for your company is largely determined by these three factors:
◊ The quality of your network infrastructure;
◊ How savvy/educated your employees are to professional and personal attempts (through spoofing, scamming, social engineering, spamming, etc);
◊ Your enforcement of strict IT Policies.
What Can You Do?
Hacking methods are constantly evolving, so your IT security systems must evolve too to keep up. The more robust and secure your network and data systems are the safer your company and client data will be.
1. If you need to safeguard proprietary networks and important client data, we recommend you:
2. Invest in a high quality “excellent” IT infrastructure, including Anti-Virus, Vulnerability Patching, Firewalls; Monitoring and Reporting, and Backup & Disaster Recovery;
3. Install and enforce a strict IT Security Policy for all branches, systems and people;
4. Ensure all devices connected to network systems are protected;
5. Periodic training and monitoring for all Employees and Contractors with any level of network access (example – how to identify and avoid common types of spoofing, scamming, spamming and other “weak-link” hacking strategies to gain access;
6. HIRE an external IT company to audit and or maintain your IT systems for you.
How Netcotech Network Solutions helps protect client systems and data
![]() Managed IT Services from Netcotech
Managed IT Services from Netcotech
- Customized solution to best support your business needs
- 24×7 Core Monitoring with Help Desk support
- Robust Anti-Virus and Intrusion Protection
- Vulnerabilities Patching
- Mobile Device Management
- Backup & Disaster Recovery
- IT Security Policy Planning and Implementation
- Application Support with 3rd party vendors
- Remote and onsite
- Effective planning for functionality, capacity and performance